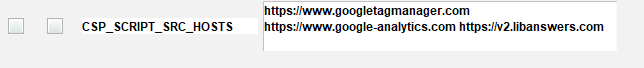
I just discovered that our upgrade on July 1 that included Sierra 6.3 implemented the new Content Security Policy (CSP) which has shut down our STACKMAP functionality and maybe some other things (at least near as I can tell in the Chrome Developer Tools window).
I understand the concept of having to add some sort of script to bypass this security policy block, but darned if I can figure it out – I’m a cataloger, not a computer whiz (even if I do have a 40+ year old BA in comp sci; that was in the days of IBM dinosaurs, pre- pretty much everything and there’s a reason I became a librarian, I can’t program my way out of a paper bag).
Does anyone have any plain English instructions to share so I can resolve our issues? We just had orientation for our new @380 1Ls and classes started TODAY. HELP, please! Thanks in advance.
Regardsz,
–Barbara Sz.
Barbara Szalkowski
Core Operations Librarian
The Fred Parks Law Library
South Texas College of Law Houston
1303 San Jacinto Street, Houston, TX 77002
713.646.1724